Elastic Engineers and Security Analysts
Take advantage of our experienced Elastic Engineers, Elastic Security analysts and advisory consultants. Sofecta experts are available when you are looking for best practice advice for Elasticsearch, or capable hands to help build your Elastic stack, or when you need advice on Cyber Security matters. Leverage our expertise when using Elasticsearch to accelerate your business processes and protect your assets from security threats.

Elastic Engineers
Are you interested in Elastic Stack technology, but need a bit of expert help? No problem, Sofecta’s experienced and Certified Elastic Engineers will help you with any technical challenge you face with the platform. Our engineers are working every day with the components of the Elastic stack, from on-prem server setups to highly automated and clustered cloud solutions.
We can assist you with anything from basic data parsing, to index management, system configuration, performance, access control, integrations, anomaly detection & Machine Learning, security detection rules, maintenance automation, and many among other aspects.
We will help you in utilizing Elasticsearch in cases of organizational search, real time log & metric analytics as well as Application Performance Monitoring instrumentation. Ask more from our sales team!

Security Analysts
Take advantage of our experienced Managed Detection and Response (MDR) security analysts to mitigate the security threats and vulnerability risks in your business. When organization-wide system visibility and security detection has been built on Elastic Security products (SIEM & EDR), you will enhance the level and extent of detections.
By utilising our security analysts to take care of the daily security platform workflow, you will be able to free up your IT team to focus on other work, leaving the analysis of alerts and tuning of machine learning models in our capable hands. Our MDR supports the daily incident investigation, preparing response actions and further security development, including:
- Intrusion Detection
- File Integrity Monitoring
- Vulnerability Detection
- Marking false positives alerts
- Building Indicator Of Compromise (IOC) blacklists
- Configuration Assessment
- Incident Response
- Regulatory Compliance
- Cloud & containers security

Security Consultants
Take advantage of cost effectiveness, competence, and flexibility with a security consultancy to enhance your business security. While our security analysts take care of operational workflows, our strategic security consultants fine tune your security policies and architecture.
Our partner network has wide variety of consultants possessing a strong real-world security and process experience. They are available to you on-site or virtually depending on your requirements. Combining technical expertise with the best security practices and recognized cyber security methodologies delivers extensive added value to your security operations and therefore to your whole business. You can leverage our expertise for instance in
- running security audits and risk assessments
- preparing action plans and designing security architectures
- security hardening processes
- Compliance Initiatives (e.g. PCI-DSS, GDPR, HIPAA, NIST)
- Identity and Access management, privilege auditing
- Secure IT Architecture, configurations, network segmentation
- Encryption, tokenization, access key management
Related content
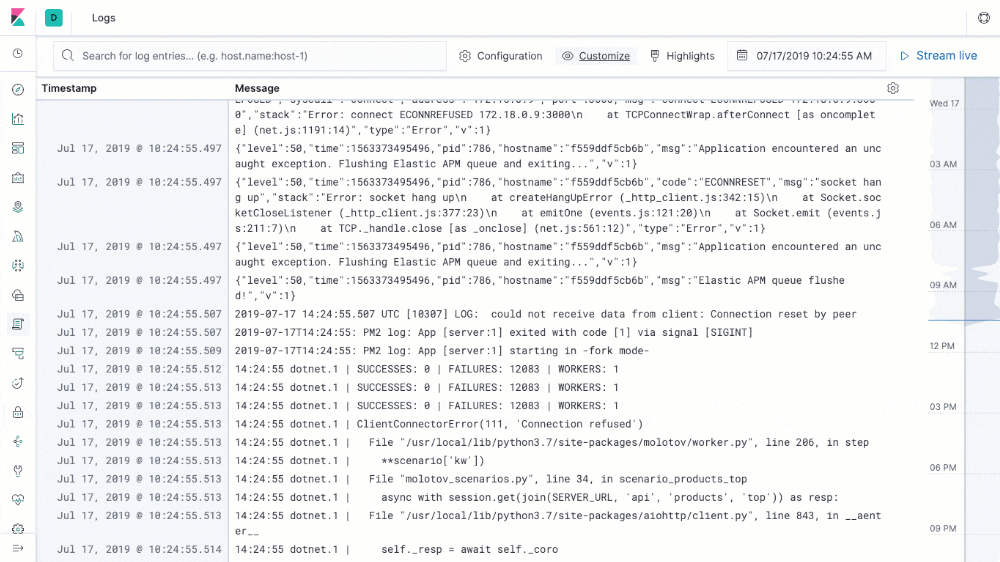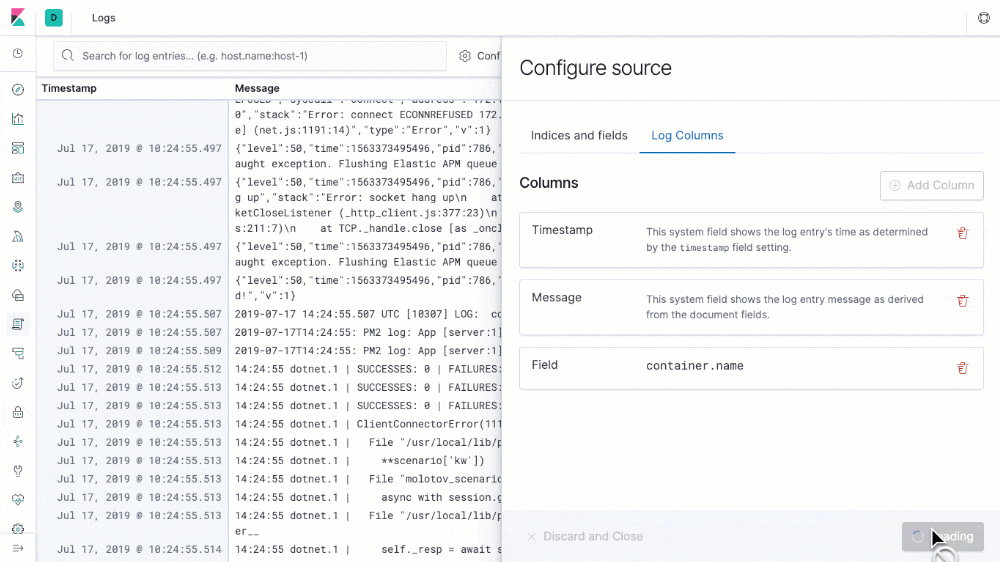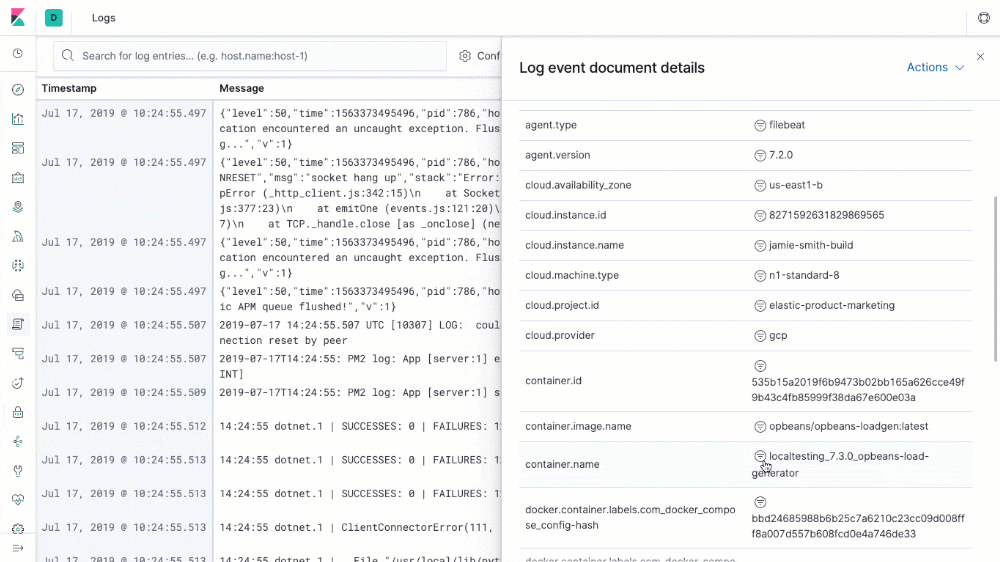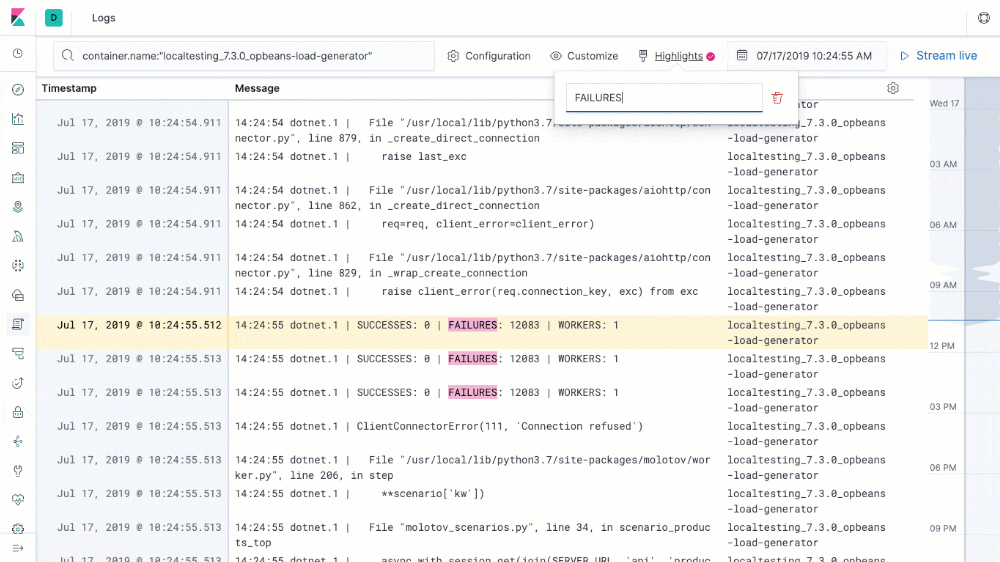
Log Management
A holistic visibility to errors, issues, patching, performance, compliance, and security turns to a challenge. How to monitor log & metric data from multiple systems in a cost-effective way?
Learn more
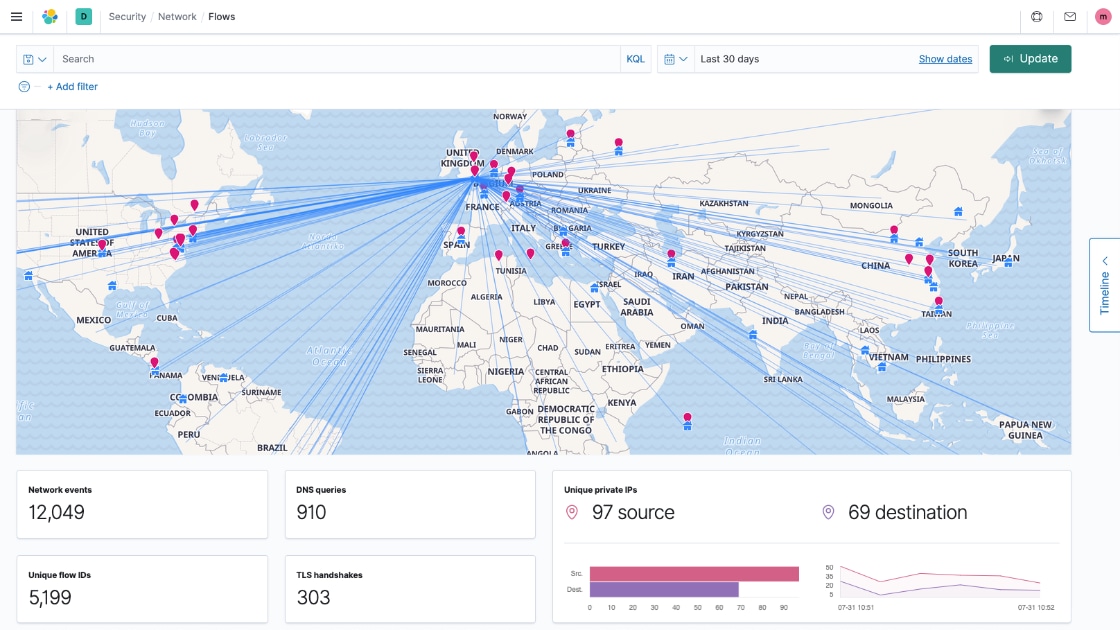
Security Information and Event Management
Transform your anomaly detection and threat hunting with intuitive Elastic Security SIEM solution and establish a holistic view to information across your environments.
Learn more
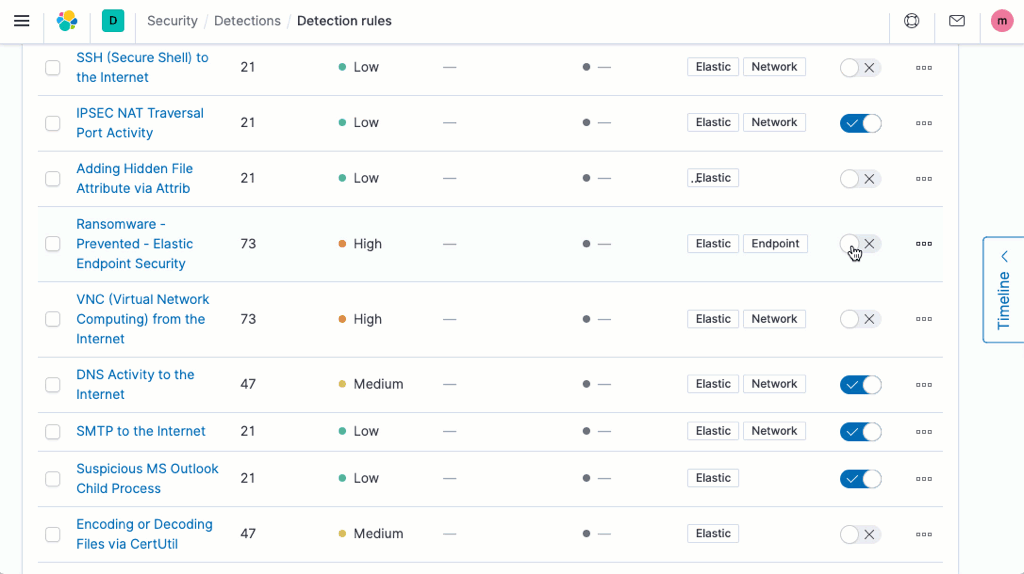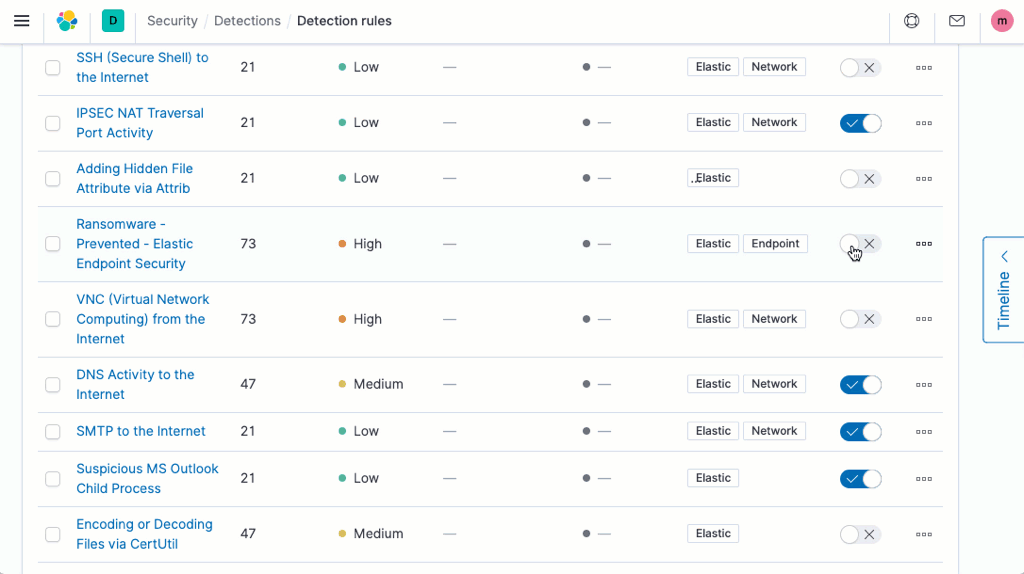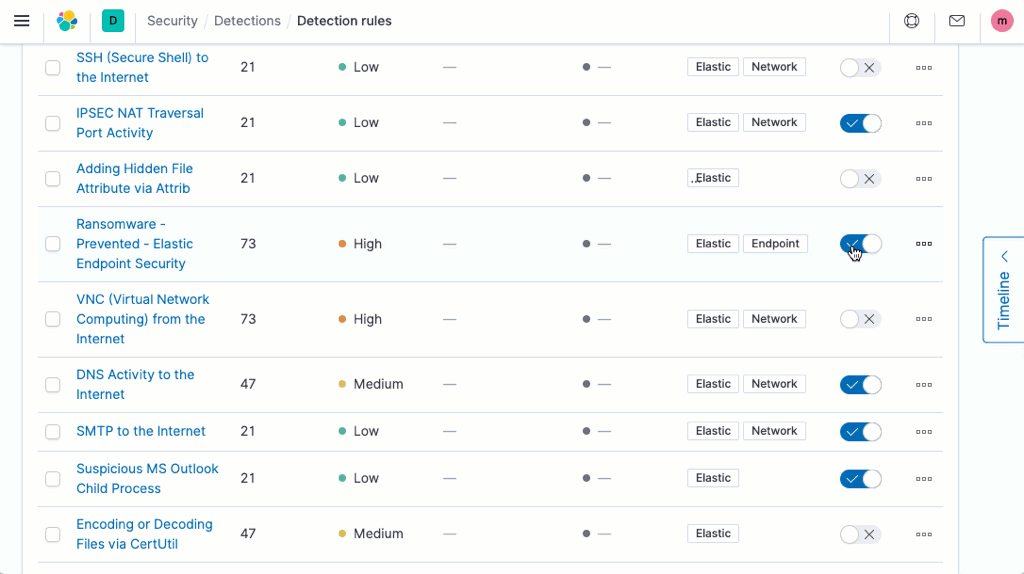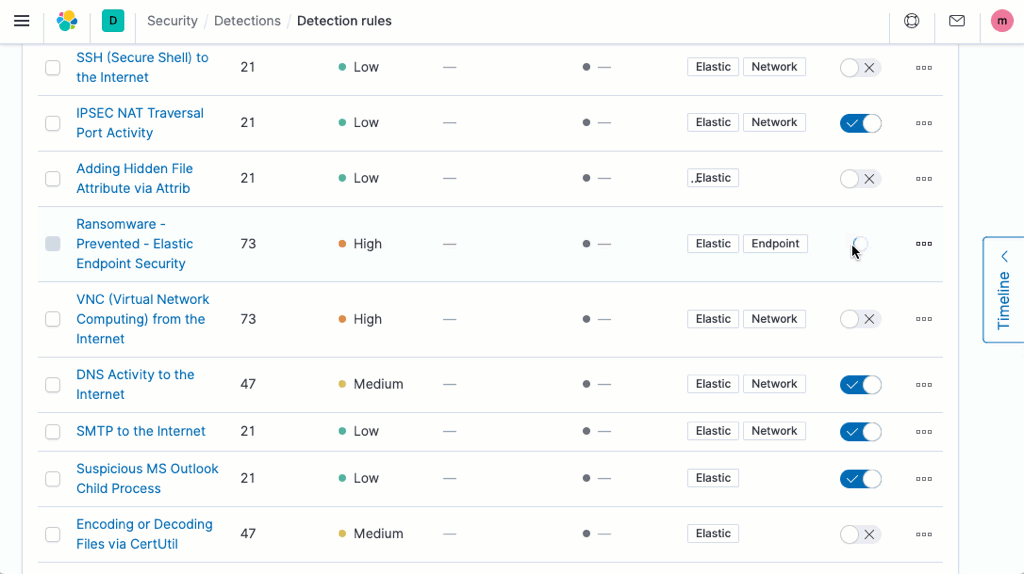
Unified protection by Endpoint Security
The threat landscape for endpoints has changed, meaning many attacks go easily unnoticed and undetected by traditional antivirus.
Learn more