Customize security solution
Enrich your Elastic SIEM with the best Open Source tools creating extra functionality, incident management and detection capability by smooth compatibility and minimal costs.

CORTEX
Cortex is an open source and free software supporting SOCs, CSIRTs and security researchers work in threat intelligence, digital forensics and incident response.
Cortex makes analysing of observables, such as IP and email addresses, URLs, domain names, files or hashes, easy by collecting and querying with a single tool instead of several. Cortex automates analysing of observables at scale through REST API and let you leverage multiple vulnerability analysers at a time. Security pro’s can actively respond to threats and interact with the constituency and other teams.
If Cortex deployed, it comes as a part of Security SaaS service full maintenance and support, and integration to Elastic Security SIEM, TheHive and MISP.

MISP Framework
MISP (Malware Information Sharing Platform) is an open source and free solution for gathering, sharing, storing and correlating indicators of compromise of targeted attacks, threat intelligence, financial fraud information, vulnerability information or even counter-terrorism information.
By generating Snort/Suricata/Bro/Zeek IDS rules, STIX, OpenIOC, text or csv exports MISP allows you to automatically import data in your detection systems resulting in better and faster detection of intrusions. When new data is added, MISP will immediately show relations with other observables and indicators, and thus getting indicators of compromise with no additional work. Over 6000 organisations worldwide are using MISP.
If MISP deployed, it comes as a part of Security SaaS service full maintenance and support, and integration to Elastic Security SIEM and/or TheHive.
WAZUH Platform
Wazuh is a free and open source solution for continuous asset inventory, security monitoring, incident response and regulatory compliance.
Wazuh is used to collect, aggregate, index and analyze security data for continuous monitoring and response to advanced threats. Wazuh agent runs at a host-level, combining anomaly and signature-based technologies to detect intrusions or software misuse. It can also be used to monitor user activities, assess system configuration and detect vulnerabilities. Wazuh can also visualize and trigger alerts for data ingested by Network Intrusion Detection Systems (NIDS) such as Suricata and Zeek.
If Wazuh deployed, it comes as a part of Security SaaS service full maintenance and support. Wazuh consist of EDR (Endpoint Detection & Response) capability and pre-canned detection rules and reporting for quick start, and to integration to Elastic Security SIEM.

ElastAlert
ElastAlert is an open source tool and simple framework for alerting on anomalies, spikes, frequency, changes, aggregations, terms, or other patterns of interest from data in Elasticsearch.
In addition of hundreds of ready-made correlation rules provided by Elastic Security, ElastAlert offers a custom querying of inconsistencies in your data. ElastAlert consist of three components; rules that are processing Elastic data according to initialized configuration; alerts that are acting on a match of rules; and enhancements for intercepting alerts it is sent e.g. to ITMS system.
If ElastAlert deployed, it comes with 20+ pre-canned rules for querying anomalies and inconsistencies of data. There are 20 alerting integrations supported for versatile endpoints. Rules and alerts maintenance can include in Security SaaS service.

Suricata
Suricata is a free and open source, robust network threat detection engine. The Suricata is capable of real time intrusion detection (IDS) in multi-gigabits traffic, inline intrusion prevention (IPS), network security monitoring (NSM) and offline pcap processing.
Suricata inspects the network traffic and complex threats using extensive rules and signature language. Suricata’s standard input and output formats like YAML and JSON integrations with Elastic SIEM and Kibana, and other database become effortless.
If Suricata deployed, it comes as a part of Security SaaS service full maintenance and support, and integration to Wazuh and Elastic Security.

Node RED
Customizing threat intelligence processes with response automation and blockings, or enrichment of your incident management and system integrations needs a low-code modeller for event-driven logic.
One of the excellent tools for multiple purposes is Node-RED. Node-RED is an open source programming tool for wiring together hardware devices, APIs and online services. It provides a browser-based editor that makes it easy to wire together flows using the wide range of nodes in the palette that can be deployed to its runtime in a single-click.
Custom logic, done by Sofecta and/or Client’s experts, can included in Security SaaS subscription.

TheHive SIRP
TheHive is an open source and free collaboration solution for SOCs, CSIRTs, CERTs and any information security practitioners. With TheHive multiple analysts can work on the same case simultaneously.
Analysts can leverage TheHive’s template engine to create repeatable tasks once and for all. SIEM alerts, phishing and other suspicious emails and other security events can be sent to TheHive for further investigation. TheHive can automatically identify observables that have been already seen in previous cases.
Analysts can analyse hundreds of observables in a few clicks by leveraging more than a hundred analysers of one or several Cortex or MISP instances. TheHive can be extended with Shuffle Open Source SOAR (Security Orchestration, Automation and Response) solution for creation and maintain of workflows and integrations.
If TheHive deployed, it comes as a part of Security SaaS service full maintenance and support, and integration to Cortex, MISP and Elastic Security.
Related content
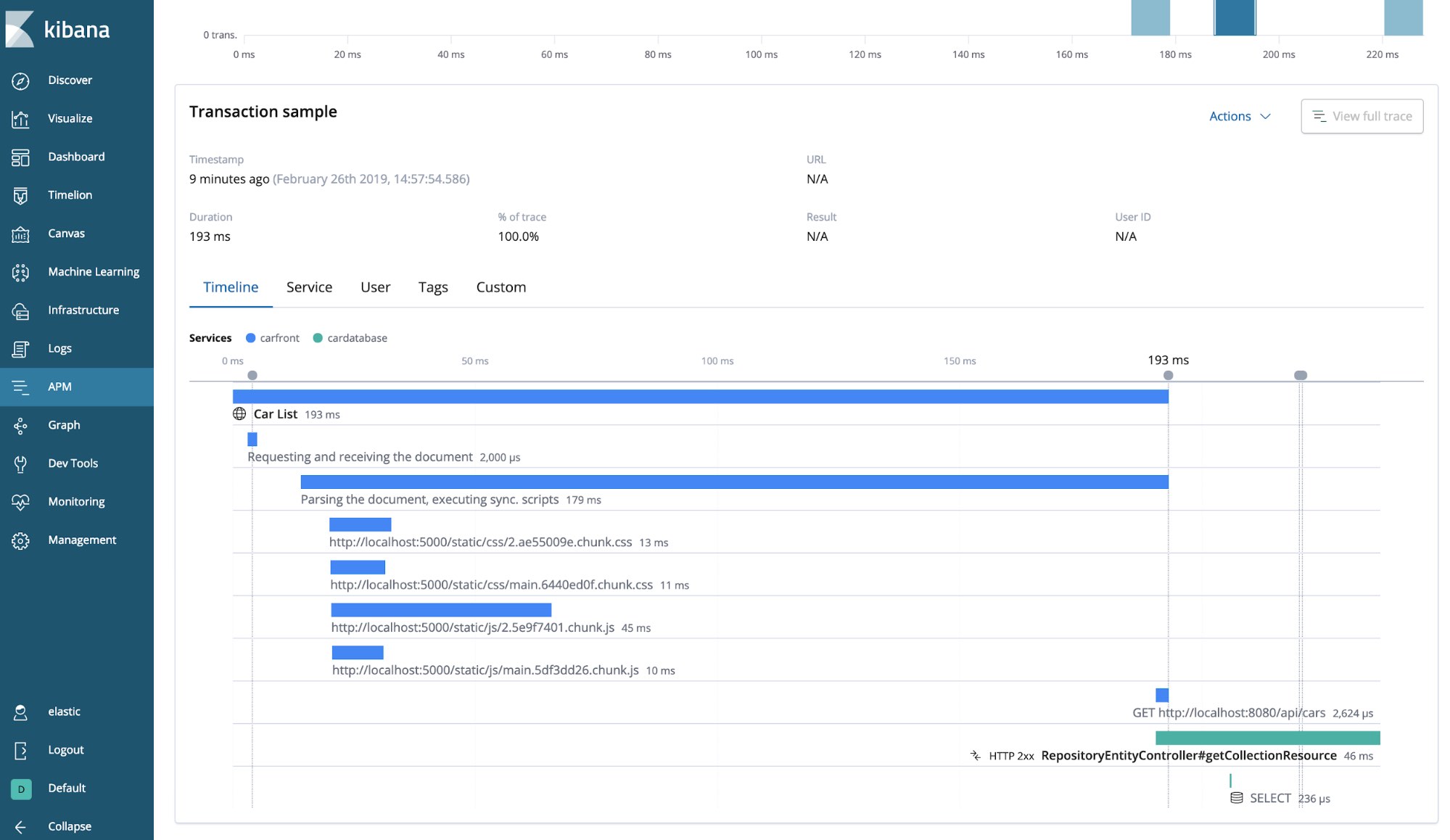
APM as a Service
Troubleshoot and monitor your code for greater efficiency and quicker releases. APM leverages a powerful data analysis platform to provide you with deep insights into your application’s operations.
Read more

Infrastructure-as-Code
Enable templated deployments and process automation, and reduce the misutilization of expert staff undertaking repetitive tasks by coding your infrastructure, built-in services, app instrumentation, and other aspects.
Read more

Container Orchestration
Accelerate the development of your business services, streamline operational capability, deploy workloads at the Edge or hybrid mode, and achieve superior security in your environments.
Read more