There are many SIEM and EDR platforms in the marketplace to choose from, but they all share some common critisicms. One of those criticisms is the number of false positive alerts. Reducing false positives involves work, which leads to the second common criticism. It takes too much dedicated staff time to analyze alerts, analyze log data, establish subscriptions with reliable threat feeds, find possible Indicators of Compromise (IoC) to check, and finally, if a threat is discovered, establish a place to discuss and document remedial action.
At Sofecta we realised the challenges our customers face and in response we proudly present “SOC Assistant” as an automation tool to reduce costs and optimize analyst’s work.
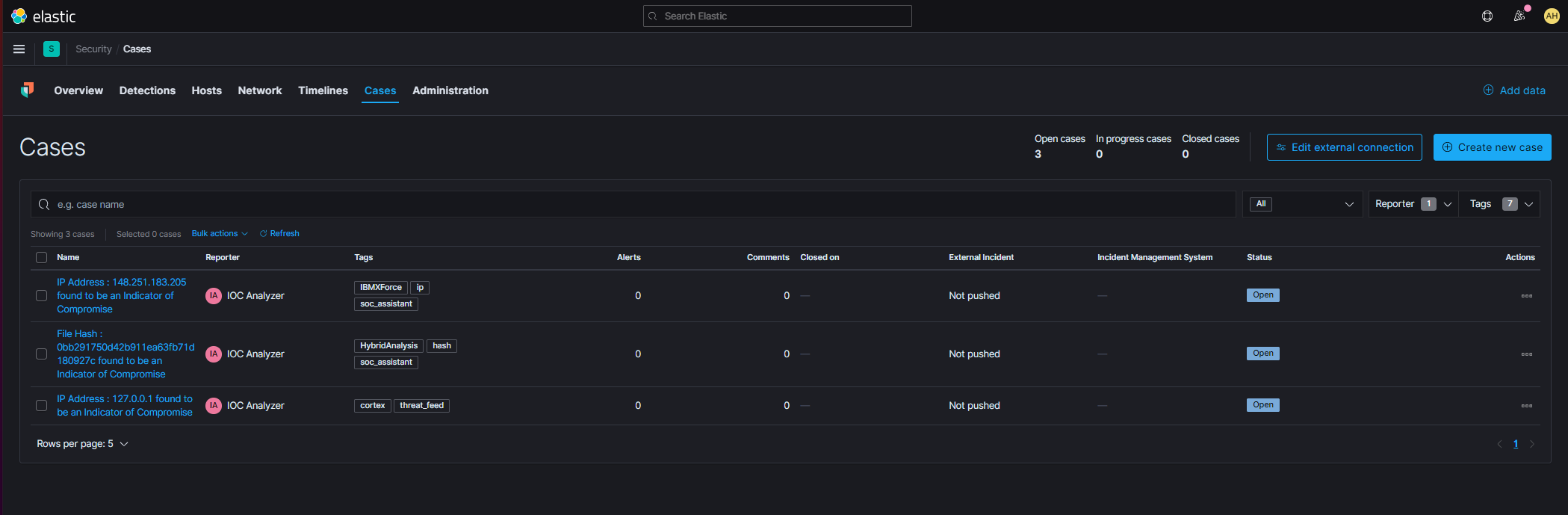
The SOC Assistant is an extension of Elastic Security Enterprise functionality, carrying out the time-consuming work of analysing alert data for all possible Indicators Of Compromise (IoC) and performing triage against a wide variety of world known threat feeds and databases.
Automated Threat Intelligence
If the SOC Assistant finds an IoC, it creates a new Elastic Security Case within Kibana automatically. An IoC represents an active threat from any observable SIEM asset, considering threat types, their behaviour and incidence. The created case includes full details of what was discovered, which threat feed reported it, and background information on the original alert that triggered the investigation.
You will be alerted immediately upon a new Case being created. As the situation would most likely represent a real and active security issue, remedial action should take place straight away. The case helps you discuss and document what was done to mitigate the threat, and when it was done. The SOC Assistant has been combined with the out-of-the-box two-way ticket management capabilities of Elastic Enterprise. Thus, if necessary, you can easily forward the case to your MDR team for further actions.
You will be alerted immediately upon a new Case being created. As the situation would most likely represent a real and active security issue, remedial action should take place straight away. The case helps you discuss and document what was done to mitigate the threat, and when it was done.
In addition to triage of alerts, the SOC Assistant can be configured to perform Threat Hunting tasks on specific types of data from your entire log data – automatically. For example, you could check all external domains accessed from within your internal networks. The SOC Assistant will check each and every one against numerous threat feeds – 24/7!
If you are feeling the pinch of keeping on top of your SIEM alerts, contact our sales team to hear more about Elastic Security SaaS-platform and advanced threat intelligence management a.k.a SOC Assistant!
Written by: Alex Hutchinson Certified Elastic Engineer and Software Architect